|
Tizen Native API
7.0
|
Key Manager
The key manager provides a secure repository protected by Tizen platform for keys, certificates, and sensitive data of users and/or their APPs. Additionally, the key manager provides secure cryptographic operations for non-exportable keys without revealing key values to clients. Since Tizen 5.0 on chosen system images, module may use ARM TrustZone technology and may rely on particular TEE (Trusted Execution Environment) implementation.
Overview
| API | Description |
|---|---|
| Key Manager Client | Provides APIs for accessing the secure repository and additional secure cryptographic operations. |
| Key Manager Data Types | Defines data types used in these APIs and provides utility methods handling them. |
It provides a secure repository for keys, certificates, and sensitive data of users and/or their APPs which are protected by Tizen platform. Additionally, it provides secure cryptographic operations for non-exportable keys without revealing key values to clients.
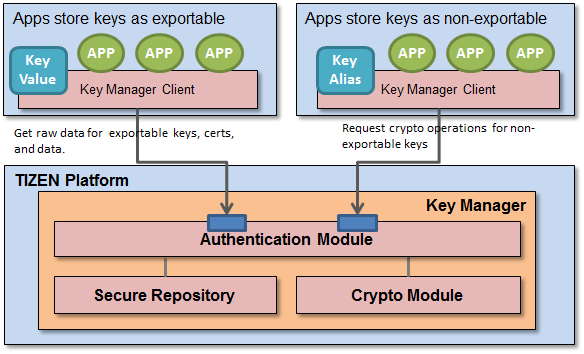
The key manager provides 2 types of API.
- secure repository APIs: These APIs provides storing, retrieving, and removing functions for keys, certificates, and data.
- secure crypto APIs: These APIs provides additional cryptographic operations (create asymmetric key pair, sign/verify signature, verify certificate). Data Store Policy: A client can specify simple access rules when storing data in Key Manager.
- Exportable/Non-Exportable: Only for data tagged as exportable, Key Manager returns the raw value of the data. If data is tagged as non-exportable, Key Manager does not return its raw value. In that case, Key Manager provides secure cryptographic operations for non-exportable keys without revealing key values to clients.
- Per Key Password: All data in Key Manager is protected by Tizen platform. Besides, a client can encrypt its data using its own password additionally. If a client provides a password when storing a data, the data will be encrypted with the password. This password should be provided when getting the data from Key Manager. Data Access Control
- By default, only the owner of a data can access to the data.
- If the owner grants the access to other applications, those applications can read or delete the data from key-manager DB.
- When an application is deleted, the data and access control information granted by the application are also removed. Alias Format
- The format of alias is "package_id name".
- If package_id is not provided by a client, the key-manager will add the package_id of the client to the name internally.
- The client can specify only its own package id in the alias when storing a key, certificate, or data.
- A client should specify the package id of the owner in the alias to retrieve a a key, certificate, or data shared by other applications.
- Aliases are returned as the format of "package_id name" from the key-manager. Supported features Since Tizen 5.0 on chosen images, the realization of module functionality can be implemented using ARM TrustZone technology. Differences in standards governing TrustZone implementation and previous software-based implementation cause following differences in module operation:
- When using TrustZone-based backend, GCM modes with 32 and 64 bit tag lengths are not supported. Global Platform TEE specification treats these configurations as unsafe and not supported.
- When using TrustZone-based backend, passing big amounts of data (encryption/decryption) to the module has additional size restriction. Now it depends on the TEEC_CONFIG_SHAREDMEM_MAX_SIZE definition, specific for given TEE implementation, minus size of key-information needed to be passed to TEE. Minimum supported value for passing data to the module is at 500 kB.